Security Policies for Every Situation
Get granular about who can access what and when. Duo lets you create custom access policies based on role, device, location, and many other contextual factors.
Instantly respond to changing user context
Protect specific apps and networks
Fully customise security policies
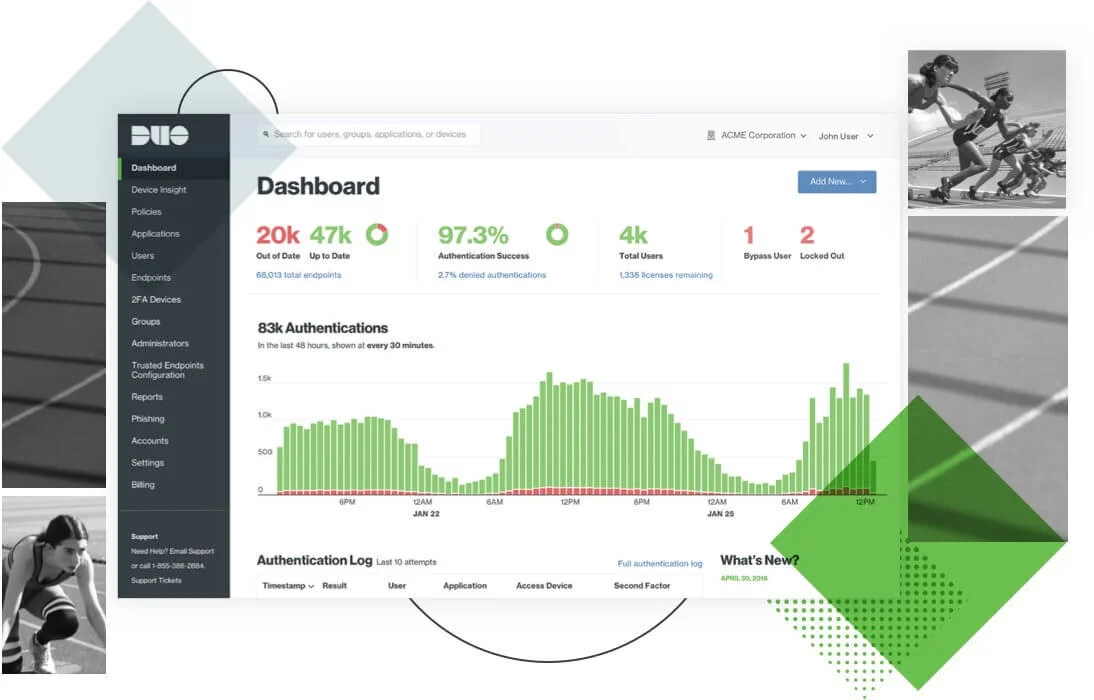
Granular Security at the Flip of a Switch
A true zero-trust strategy changes the level of access or trust based on contextual data about the user or device requesting access. It also limits access to only users that really need it. With Duo, you can set up detailed policies in minutes via a simple, intuitive administrator dashboard, and manage rules globally or for specific applications or user groups.
Verify Trusted Users
Every user has a different use case for access to your applications, and Duo handles them all with ease. Detect user location, device, role, and more at every login, set security policies based on these attributes, check for anomalous access, and continuously monitor policy efficacy — all without interrupting your users' daily workflows.
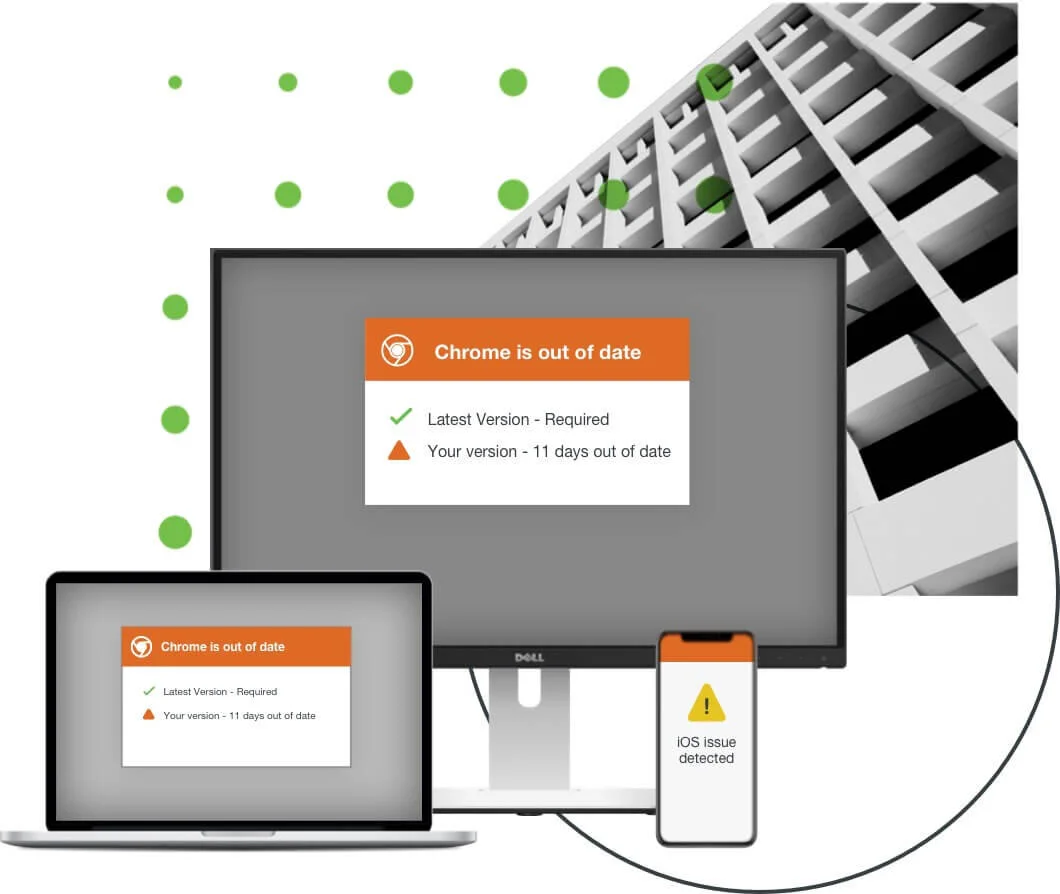
Secure Access Based on Device Trust
Protect against potentially compromised or risky devices accessing your applications and data. Apply security policy across every device — managed or unmanaged. Duo lets you define permissions based on OS and individual device settings, and automatically notify (or even block) users when their software is out of date.
Implement Policies by Application
Take a big step toward zero trust by making sure the right people have access to the right tools. Duo's application-specific controls make it easy to onboard contract employees, change access permissions, protect high-value information with stringent security policies, and more.